“… we reserve the right to act unilaterally, as we have done relentlessly since I took office […] while making sure that other nations play by the rules …”
– Barack Hussein Obama II, 44th US-President, January 20, 2015
The US-magazine “Foreign Policy”, which claims to be “reporting [from] inside the foreign policy machine”, on 20/11/13 published an article titled: “Exclusive: Inside America’s Plan to Kill Online Privacy Rights Everywhere“. It discloses the United States’ strategy to prevent, that the 193 members of the United Nation’s General Assembly will vote for an universal human right to online privacy in coming December.
Brazil and Germany had introduced to the UN General Assembly their draft resolution in early November and it became co-sponsored by 55 countries, so it seemed guaranteed that the resolution would pass – wouldn’t it?

Lobbying behind the scenes
The US decided not to openly oppose the resolution, but let its ‘Five-Eyes’ intelligence sharing alliance of UK, Canada, Australia and New Zealand do the job. Therefore these countries were given a confidential list of instructions – U.S. Redlines – in order to water down the language of the resolution.
Redline #1: “Clarify that references to privacy rights are referring explicitly to States’ obligations under ICCPR and remove suggestion that such obligations apply extra-territorially.”
This United Nation’s “International Covenant on Civil and Political Rights”1 (ICCPR) determines:
Article 17
1. No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence, nor to unlawful attacks on his honour and reputation.
2. Everyone has the right to the protection of the law against such interference or attacks.
The original resolution text repeats:
Reaffirming the human right to privacy, according to which no one shall be subjected to arbitrary or unlawful interference with his/her family, home or privacy, or correspondence,
The US amendment complicates:
Reaffirming the human privacy rights of individuals under Article 17 of the ICCPR, that is to privacy and not to be subjected to arbitrary or unlawful interference with their privacy, family, home or correspondence,
Spin doctor wickedness
NB: only the term “the human right to privacy” but not “the human privacy rights” defines an universal right!
And according to the US-plan there will be none: “As the text currently reads, it suggests that states have international human rights obligations to respect the privacy of foreign nationals outside the U.S., which is not the U.S. view of the ICCPR.” As a consequence for the USA “extraterritorial surveillance” and mass interception of communications, personal information, and metadata do not constitute a violation of human rights.
Further US-instructions are:
Redline #2: “Clarify that the focus of the resolution is on “unlawful” or “illegal” surveillance and interception of communications.”
Redline #3: “Clarify that violations of privacy rights not necessarily violate freedom of expression.”
Protecting superior knowledge
What 55 states spied upon want to say:
“Deeply concerned at the negative impact that surveillance and/or interception of communications, including extraterritorial surveillance and/or interception of communications, in particular when carried out on a mass scale, may have on the exercise and enjoyment of human rights.”
What the ‘Five Eyes‘ spy-states understand [structure, emphasis of the original draft kept]:
“Deeply concerned that human rights violations and abuses that may result from the abuse of information acquired through the conduct of any surveillance or interception of private communications, including extraterritorial surveillance or interception of private communications, their interception, as well as the collection of personal data, including particular massive surveillance, interception and data collection, […]
recognizing that the exercise of the right to privacy rights is often understood as an essential requirement for the realization enjoyment of the rights to freedom of expression and to hold opinions without interference, and one of the foundations of a democratic society” .
These US-inspired amendments to the original intention, namely to curb excessive surveillance, are supposed to result in an unintelligible statement, comparable to the ‘Terms and Conditions’ the users always click-away without second thought.
The US-plan targets to change the resolution’s subject to condemning only illegal surveillance – which the US-government claims it never, ever does. So if it’s authorized by US statute, overseen by the US-Congress, and approved by American courts – why can’t the world accept, that collecting information on billions of people around the globe is necessary to defend freedom and democracy?
“The hidden hand of the market will never work without a hidden fist — McDonald’s cannot flourish without McDonnell Douglas, the builder of the F-15. And the hidden fist that keeps the world safe for Silicon Valley’s technologies is called the United States Army, Air Force, Navy and Marine Corps.”
— Thomas Friedman 1999, New York Times
Maintaining Global IT-Supremacy
No sane Tanzanian would believe, that a herd of impalas could enter into an arrangement with a pack of lions. It is to be seen which resolution text eventually will be presented to the General Assembly of the United Nations to decide upon. Just stay tuned, the KUKU Trust will keep you informed.

Lion and Impala, intensifying bilateral relations – karibuni Serengeti!
This metaphor depicts pretty well how Tanzanians see their relations with the developed countries. The anger of Germany on the other side, was rather caused by the fact that she had not been invited a place at the banquet.
You might also say that the Impalas also had their moment of glory, when they believed back in 2005 that they could determine the future of ICT by their Tunis Commitment 2005:
 |
 |
 |
1. We, the representatives of the peoples of the world, have gathered in Tunis from 16‑18 November 2005 for this second phase of the World Summit on the Information Society (WSIS) …
2. We reaffirm our desire and commitment to build a people-centred, inclusive and development-oriented Information Society …
3. We reaffirm the universality, indivisibility, interdependence and interrelation of all human rights and fundamental freedoms, including the right to development …
Indeed, back in 2005, inside United Nations committees, the bold vision of a Golden Age of the Global Information Society, by the means of “collaborative development, interoperative platforms and free and open-source software“, was propagated – even a “human right to development”!
Alas today a different future unfolds:
“The Golden Age of SIGINT”
- SIGINT: intelligence obtained through the interception of transmission signals
- HUMINT: covert intelligence-gathering by agents
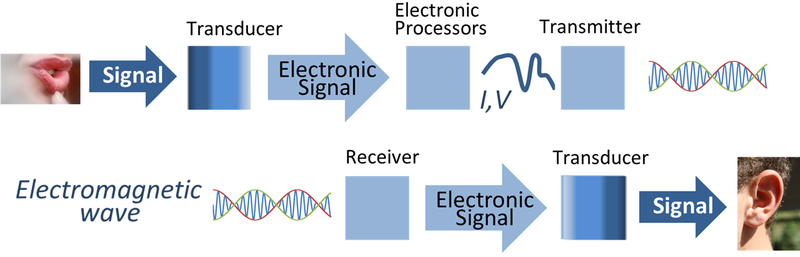
One century ago first radio transmissions started to fill the air with radio waves. Today billions of people send and receive radio impulses around the clock, as many don’t even switch-off their mobile phones while they sleep. But unlike in a personal meeting (HUMINT), where people can arrange that their face-to-face remains private, their virtual meetings via radioed electronic signals (SIGINT) are overseen by:
- The service providing company – also collecting connection charges
- Intelligence agencies – keeping telecommunication under surveillance
On 22/11/2013 the New York Times published a top-secret NSA document which contains the SIGINT-Strategy 2012 –2016 of the undisputed global spy-master. It reveals their plan to further develop and extend their supremacy in the electronic realm – which explains why the US-government will never allow a universal human right to online privacy!
 The NSA-logo depicts the US-heraldic animal
The NSA-logo depicts the US-heraldic animal
clutching at the master-key to unlock all privacy.
The NSA’s prime focus2 is to “dramatically increase mastery of the global network” by “dominating the environment” of global electronic computation and communication. The Agency is aware that individuals or states will try to defend their privacy, therefore their Strategy 2012 –2016 targets to:-
2.2. (TS//SI//REL) Defeat adversary cybersecurity practices in order to acquire the SIGINT data we need from anyone, anytime, anywhere.
The Agency has to ensure that nobody can purchase a useful encryption software:
2.1.2. (S//REL) Counter the challenge of ubiquitous, strong, commercial network encryption
Independent development of encryption software must be sabotaged 3 – if this can not be achieved remotely – by SIGINT – e.g. through malicious computer code like viruses, troyans…, then secret agents – HUMINT – will be deployed to complete the mission – by all means:
2.1.3. (TS//SI//REL) Counter indigenous cryptographic programs by targeting their industrial bases with all available SIGINT and HUMINT capabilities
The CIA has a rich history in establishing Front Companies4 with the purpose to facilitate and cover-up its clandestine extra-territorial operations:
2.1.4. (TS//SI//REL) Influence the global commercial encryption market through commercial relationships, HUMINT, and second and third party partners
Framed Development
Concluding from the secret files, the future ITC-development is just being transformed into another trickle-down agenda, where the many poor are supposed to prosper within a framework set by the few rich.
This ever increasing disparity made Pope Francis, the spiritual head of the Catholic Church, actually question the validity of such “trickle-down theories which assume that economic growth, encouraged by a free market, will inevitably succeed in bringing about greater justice and inclusiveness in the world“. He warned, that such “ideology” – “which has never been confirmed by the facts” – “expresses a crude and naïve trust in the goodness of those wielding economic power and in the sacralized workings of the prevailing economic system“.
A system which rules rather than serves
A new tyranny is thus born, invisible and often virtual, which unilaterally and relentlessly imposes its own laws and rules.
— Pope Francis’ apostolic exhortation of 28/11/2013
While condemning the “ruthless guise in the idolatry of money and the dictatorship of an impersonal economy lacking a truly human purpose“, Pope Francis urges us to adhere to “a non-ideological ethics – would make it possible to bring about balance and a more humane social order.”
Uhuru OS – the key to an ethical Digital Culture
In special regard to Africa, Francis’ apostolic exhortation reiterates the position of the African bishops, who pointed out years ago, that there have been frequent attempts to make the African countries “parts of a machine, cogs on a gigantic wheel. This is often true also in the field of social communications which, being run by centres mostly in the northern hemisphere, do not always give due consideration to the priorities and problems of such countries or respect their cultural make-up”.
All right; so let’s take back our Tanzanian sovereignty “in the field of social communications” then! Obviously self-reliance is the only way to defend our human rights to online privacy as well as to IT-development.
Our Uhuru OS lets its users enjoy four essential freedoms:
- The freedom to run the Uhuru OS, for any purpose
- The freedom to study how the Uhuru OS works, and change it so it does your computing as you wish. Access to the source code is a precondition for this.
- The freedom to redistribute copies of Uhuru OS so you can help your neighbour.
- The freedom to distribute copies of your modified versions of Uhuru OS to others. By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this.
“The English people have a proverb which says, ‘He who pays the piper calls the tune’. How can we depend upon foreign governments and companies for the major part of our development without giving to those governments and countries a great part of our freedom to act as we please ?”
— Julius Kambarage Nyerere, Arusha Declaration, 05/02/1967
Breaking News 15/08/2014:
With the meta-goal of “Mastering the Internet” the Anglo-American spy agencies are scanning entire countries (27 nation-scans completed), in order to look for vulnerable network infrastructure and to attack every possible system they can. Learn more about The HACIENDA Program for Internet Colonization.
Update 04/09/2014:
The U.S. Justice Department believes that it is vested with a “global jurisdiction” to access data from any computer around the world – for the reason that the contrary would be “not practical”.
Update 11/07/2015
FBI director Jim Comey wants every device and software manufacturer to volunteer to create backdoors for the U.S. government to snoop on global communication.
Update 19/01/2016
The UK Government promotes their official encryption for voice-calls – which was designed by their secret service! It gives them undetected and unrestricted access to all your phonecalls.
“The economic prosperity that our nation enjoys today is largely founded in the Information Age and in our global leadership in information technology. Our continued leadership and prosperity in the global economy may well hinge on our national commitment to act as leaders in bringing integrity and responsibility – information assurance – to the global information environment we have helped to create.”
His computer was infected after clicking a (bogus) LinkedIn invitation of a non-existent employee of the European patent office. That allowed the intruders to follow all of the professor’s digital movements, including his work for international conferences on security.
William Blum, a former employee of the US Department of State, claims in his book “Killing hope: US military and CIA interventions since WWII”, that USAID maintains “a close working relationship with the CIA, and that Agency officers often operated abroad under USAID cover“.
One thought on “US Plan to destruct online Privacy Rights everywhere”
Comments are closed.