On 06/06/2013, The Washington Post and The Guardian started publishing classified documents revealing that the National Security Agency (NSA) and the FBI are tapping directly into the central servers of telecommunications companies and at least nine leading U.S. Internet companies:
Apple, Microsoft, Google, Yahoo, Facebook, PalTalk, AOL, Skype, YouTube.
Using such facilities means that audio and video chats, e-mails, photographs and documents can be copied and analysed – inclusive connection logs – by a third party.

“They quite literally can watch your ideas form as you type” (Snowden)1
The New York Times stressed that “the disclosures provided the most detailed confirmation yet of what has been long suspected about what the critics call an alarming and ever-widening surveillance state.”
By accepting such a flat banality2 you might lose sight of the forest for some trees:
- Players: The operations aren’t sanctioned by ‘the state’ but instead run by “the ‘Deep State’ behind U.S. democracy“, authorised by classified order of a top-secret Foreign Intelligence Surveillance Court.
- Methods: The news are mixing up two different kinds of surveillance:
- Wire-tapping – eavesdropping on identified targets through backdoors to the facilities of the telecommunication industry.
- Big Data mining – according to McKinsey “the next frontier for innovation” – is promising big business. All global data of sources like;
- healthcare institutions,
- the public sector,
- retail shops,
- manufacturing and
- personal data, -location data
… are supposed to flow together into one big ocean of unstructured Big Data. To identify structures in that sea and catch the fish, i.e. separating signal from noise, the NSA is using a highly sophisticated tool named “Accumolo” – which is based on Google’s BigTable data model.
Moreover the according US-programs UPSTREAM3 and PRISM4 work hand-in-hand with the British Tempora programme, together constituting “the largest programme of suspicionless surveillance in human history“. Allied countries participate by secret arrangement.
“How Big Data is changing almost everything”
While the mainstream media made the emotions boil over about this outrageous scandal, most remained silent about the Bilderberg Meeting which was taking place at the same time in Hertfordshire, UK from 6 to 9 June.
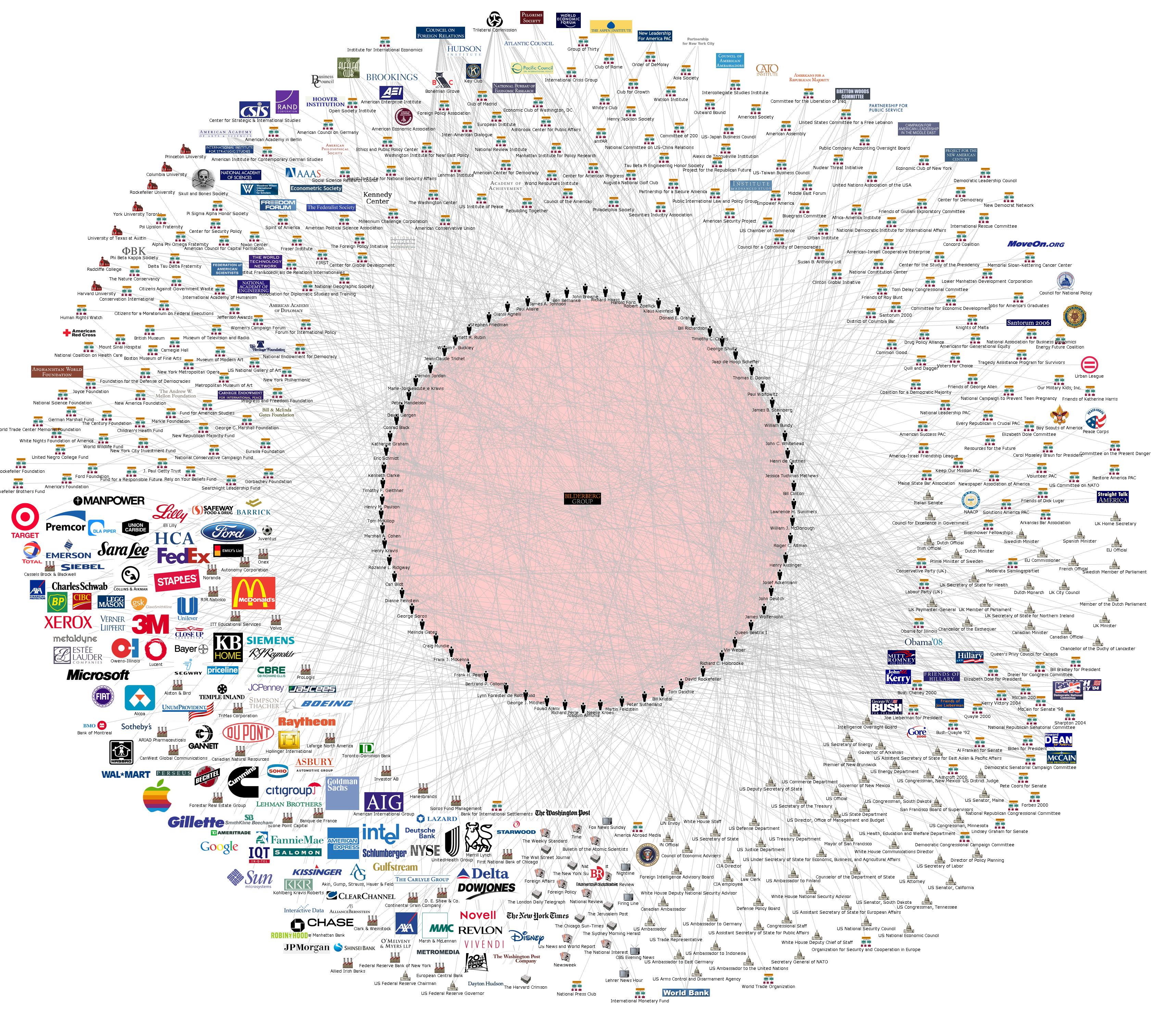 Shielded against public curiosity by massive British security forces, the “the most influential group in the world“, consisting of hand-picked bankers, businessmen, politicians, media bosses and defence officials, was gathering in private(!), among them:
Shielded against public curiosity by massive British security forces, the “the most influential group in the world“, consisting of hand-picked bankers, businessmen, politicians, media bosses and defence officials, was gathering in private(!), among them:
- Craig J. Mundie, Senior Advisor to the CEO, Microsoft Corporation,
- Eric E. Schmidt, Executive Chairman, Google Inc.,
- Peter A. Thiel, President, Thiel Capital, Founder of PayPal online payment system and Facebook investor
- Jeff Bezos, Founder and CEO, Amazon.com
- David H. Petraeus, General, retired Director of the CIA
- Christine Lagarde, Managing Director, International Monetary Fund
- Henry A. Kissinger, National Security Advisor.
Just check the entire guest list to realise how much Big Data accumulates under the control of this elitist group and relate it to the following topics of their agenda:
- How big data is changing almost everything
- Cyber warfare and the proliferation of asymmetric threats
- Online education: promise and impacts
- Africa’s challenges
Africa’s challenges?
The Guardian newspaper published details about an NSA data-mining tool called “Boundless Informant”, which organizes and maps records of communications collected from computer and phone networks.
Its “heat map” shows countries less surveyed by NSA in green to most surveyed in yellow, orange and red. Iran and Pakistan are ‘red hot’ while the Scandinavian countries show ‘cold dark-green’ colour – which stands for a low data harvest.

The white arrow in the map points to Tanzania, which already ‘progressed’ to a warmer green, maybe due to the implementation of a digital ID-system with biometrics on its population and the good network coverage.
The ‘African Challenge’ might be to roll-out more ITC-infrastructure in the mostly dark-green areas of Black Africa – a prerequisite to monitor the privatisation process or to obtain Big Data.
Conveniently Madame Lagarde was present, the Managing Director of G8 taxpayer’s money in the International Monetary Fund5 and a stakeholder in the World Bank’s Millennium Development Goals and Poverty Reduction Programmes.
A footnote to history, Obama was approved by the Bilderberg Elite in 20086 which gives us a clue who runs the ‘state within’.
Deep State policy – the merger of state and corporate power7
Prof. Chomsky points out the usefulness of close relations to the ‘state sector for ‘the ‘private sector’: “Computers and the Internet were almost entirely within the state system for about 30 years – research, development, procurement, other devices – before they were finally handed over to private enterprise for profit-making.”
On the other hand, the government is indispensable for the management of public opinion. Since the 1920ies “the manufacture of consent” was esteemed as useful and necessary for a cohesive society, because “the common interests” would not become obvious to the masses, but only become clear to experts upon careful analysis of the collected data – the opinion poll was implemented. Nowadays “Big Data is changing almost everything”:
“The challenge for the overseers had shifted from […] the tedious labor of administrative records to that of information systems designed to produce automated, continuous, frictionless, perfect accounts available for zoom-in detail and zoom-out patterns any time, all the time, everywhere.”
– Shoshana Zuboff
The Hyper-Connected Digital Lifestyle: Friend or Foe?
In the 21st century it is no longer necessary to “pull” information from the masses. Corporations employ the best creative minds to change ideas and manufacture new trends: “becoming a celebrity” is the career choice for half of 16-year-olds, who flood the ‘social networks’ with their most personal data to market themselves.
The latest survey in the UK indicates that the average person likes to spend one-third more time per day looking at his/her phone (119 min) than with his/her partner (97 min). Alas this smart mate has been exposed as undercover agent.
“If the government demanded that we all carry tracking devices 24/7, we would rebel. Yet we all carry cell phones…
If the government demanded that we give them access to all the photographs we take, and that we identify all of the people in them and tag them with locations, we’d refuse. Yet we do exactly that on Flickr and other sites.”
Bruce Schneier, chief security technology officer for British Telecom8
Apple (AAPL), Google (GOOG) and Microsoft (MSFT) established a global monopoly9 for computer operating software. The customer has to buy an all-or-nothing package: Before allowing the use of ‘Windows 8’, iOS, or Android all three corporations dictate elaborated terms and conditions which transfer the control to them.
A user can’t say: I allow this company to process my data, but I don’t allow them to handle my phone or my ID to any or a particular 3rd party. Or I’m fine with statistic usage, but like to block advertisement. Its just “take it or leave it”
90% of the world’s data was created in the last two years10 11
The corporate data sets are exploding in size. Additional data is increasingly being gathered by ubiquitous information-sensing mobile devices, aerial sensory technologies (remote sensing), software logs, cameras, microphones, radio-frequency identification readers, and wireless sensor networks.
Only a huge collection of data from various sources constitutes a Big Data base total enough to produce reliable intelligence for decision making. To achieve completion the agencies and corporations resort to the same practise which has been outlawed for ordinary people as ‘act of piracy’ – filesharing:
US Agencies Said to Swap Data With Thousands of Firms
“Thousands of technology, finance and manufacturing companies are working closely with U.S. national security agencies, providing sensitive information and in return receiving benefits that include access to classified intelligence, four people familiar with the process said.”
A leaked NSA-document described the new tool as “the most prolific contributor to the President’s Daily Brief”, the Obama administration defended it as “a critical tool in protecting the nation from terrorist threats.”
“Governments should not have this capacity. But governments will use whatever technology is available to them to combat their primary enemy – which is their own population.”
– Noam Chomski 12
Any questioning alike “shouldn’t a person’s own data also be protected by copyright”, is silenced by the answer:
No comment on matters pertaining to national security.
A fundamental transformation of society is best implemented dictatorial13 – if terror-stricken citizen rally behind a leader.The ‘under attack’ situation suppresses a public debate about the proportionality of data collection and if individual particulars are more than just unclaimed objects.
Information Warfare has become an imperative weapon in the Global War on Terror and an important element of the global US-military Full Spectrum Dominance doctrine..
Alas the ‘War on Terror’ narrative is contradicted by the leaked Boundless Informant heat map, indicating the USA herself is extensively subjected to NSA surveillance. There must be a more plausible explanation.

“Scientia est Potentia” – Knowledge is Power
The seal of the US-Information Awareness Office contains a Latin phrase. “Scientia potentia est” derives from a 1658 publication by Thomas Hobbes. As a young man he was a secretary to Sir Francis Bacon who in 1597 had formulated it slightly different: “ipsa scientia potestas est” – knowledge itself is power.
- “Potestas” is a power attained constitutionally by and for the public good; equivalent with abililty, capacity, possibility, opportunity, public authority, rule, magisterial power, permission.
- “Potentia” means power too but it has the connotation of private might and authority. Influence (potential) attained by any means (even illegal) and used for personal ends.
“The architects of power in the United States must create a force that can be felt but not seen. Power remains strong when it remains in the dark; exposed to the sunlight it begins to evaporate.” [Hunt, 9/1/2009, pp. 8]
– Samuel P. Huntington14
Our Defence: substituting Potestas for Potentia
“No one shall be subjected to arbitrary interference with his privacy, family, home or correspondence. Everyone has the right to the protection of the law against such interference.”
– Universal Declaration of Human Rights, Article 12
2 days before these press revelations started, on 04/06/2013, the United Nations Special Rapporteur Frank La Rue went public with his report to the Human Rights Council, calling for more global attention to the widespread use of surveillance technologies in violation of the human rights to privacy and freedom of expression:
“Who are the authorities mandated to promote the surveillance of individuals? What is the final destiny of the massive amounts of the stored information on our communications?”
The UN jurist criticised the national laws regulating communications surveillance as often “inadequate or nonexistent.” He seems unaware, that the human rights are attacked in a “pincer movement” of corporate and state win-win interests:
- Corporations, lead by Google, developed global user-monitoring for profit.15 Sharing ‘vital’ information with state instruments gives them systemic relevance – “too big to fail”.
- In return the US-government and satellite regimes – in total disregard of individual privacy – globally defend ‘free markets’ and ‘business secrets’ as inviolable sanctity.
A striking example for the revolving door between US-government and US-corporations is, that Dropbox Inc., a global data service, appointed Condoleezza Rice as director. As Security Adviser to President Bush, she directly responsible for the war with Iraq and authorized the warrantless wiretap of UN Security Council members.
A successful defence requires bidirectional reverse action:
- The Law Code – amending the Human Rights by making each individual own the copyright on personal data
- The Computer Code16 – safeguarding A. – ensuring that citizens can opt for hard- and software – even basic internet facilities – scrutinized and certified by their government.
The irony is, that neither Microsoft, nor Apple nor Google will agree to a perusal of their code – while its just the integration of publicly scrutinised open source code which makes ‘Mac OS X’© or Android© more secure and stable than Windows©!
Consequently the most inexpensive way to obtain a safeguarded PC is to entirely rely on Free and Open Source Software (FOSS) and to support the development of the the People’s PC.
Such a milestone towards national digital sovereignty can be accomplished in revenue neutrality – provided Tanzania would stop to indiscriminately exempt the entire kaleidoscope of computer hard- and software from customs, taxes, even VAT, but in the future privilege only such products which are in compliance with national regulations about computer freedoms.

“The Greek people are anarchic and difficult to tame. For this reason we must strike deep into their cultural roots: perhaps then we can force them to conform. I mean, of course, to strike at their language, their religion, their cultural and historical reserves, so that we can neutralize their ability to develop, to distinguish themselves, or to prevail; thereby removing them as an obstacle to our strategically vital plans in the Balkans, the Mediterranean, and the Middle East.”
– Henry Kissinger, core member of the Bilderberg Group17
Update: No ‘need to know’ – top secret ICT espionage methods revealed
Latest published insights into Snowden’s documents can only lead to one grim conclusion: Today the entire use – and development – of ICT takes place under the control of a small US-British elite.
“Those not already briefed were gobsmacked!”
– internal agency memo noting the reaction among British analysts to a presentation about the NSA’s possibilities.
Back in the mid 1990s the NSA lost a heated national debate about inserting into all PCs a government back door called the Clipper Chip. Thereafter the agency started “to leverage sensitive, co-operative relationships with specific industry partners”.
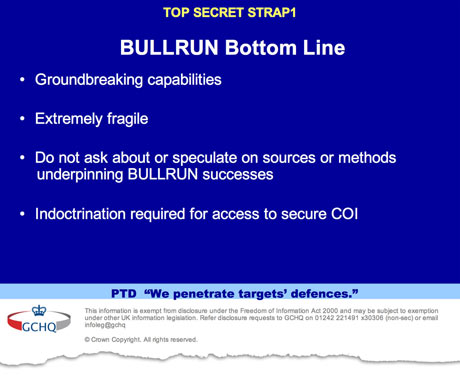
“There will be no ‘need to know‘”, intelligence workers were told, as “loss of confidence in our ability to adhere to confidentiality agreements would lead to loss of access to proprietary information that can save time when developing new capability“.
Compromising hardware and software standards
A covert collaboration with technology companies and internet service providers has been established, in order to weaken IT-standards and -methods, even influencing or sabotaging product designs to intentionally contain exploitable flaws.
“Eventually, NSA became the sole editor”
– quoted from a secret document, describing how a security standard was developed, then issued by the US National Institute of Standards and Technology (NIST) and approved for worldwide use in 2006.
Meanwhile NIST “strongly” recommends against even using one of these standards!
As a matter of fact today most commercial software code contains premeditated vulnerabilities, to ensure that government-hackers can read-out the personal data of Smartphones or PCs, and deliberate imperfections, to ensure that the encryption of communication remains weak and easy to decrypt.
Interestingly the NSA’s codeword for its computer security penetration programme is “Bullrun” while the GHCQ named their counterpart “Edgehill” – both historical names of opening battles which started the US- or English civil war!
Quoting from The Guardian newspaper:
- NSA and GCHQ unlock encryption used to protect emails, banking and medical records
- $250m-a-year US program works covertly with tech companies to insert weaknesses into products
- “By deliberately undermining online security in a short-sighted effort to eavesdrop, the NSA is undermining the very fabric of the internet”; Bruce Schneier, security expert.
The US National Security Agency reacted to these revelations with the following statement:
“The Department [of Defense] does ***not*** engage in economic espionage in any domain, including cyber.”
– NSA spokesman; 30. Aug. 2013
Thereafter the Brazilian newspaper Globo published a report, based on leaked documents from Edward Snowden, that the NSA targeted Brazil’s state-run oil firm Petrobras. Other objects of espionage were Google and the Belgium-based Society for Worldwide Interbank Financial Telecommunication, an organization better known as SWIFT.
‘Follow The Money’: NSA special branch spies on international payments
According to documents seen by a German magazine, the NSA monitors not only SWIFT, but nearly all international payments, banking and credit card transactions. The agency set up its own financial database (Tracfin) to track money flows through a “tailored access operations” division called “Follow The Money” (FTM).
“It is not a secret that the Intelligence Community collects information about economic and financial matters; […]
to understand economic systems and policies and monitor anomalous economic activities is critical to providing policy makers with the information they need to make informed decisions that are in the best interest of our national security.”
– National Director of Intelligence; 9. Sep. 2013
So its not about “terrorism” any more, but “best interest“?
Moreover there seems “no ‘need to know'” for the people of the United States, since the same National Director of Intelligence, James Clapper, testified under oath before the US-Senate in March 2013 as follows:
Sen. Ron Wyden: “Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?”
Dir. Clapper: “No, sir … not wittingly.”18
There are alternatives to IMF-style programs: Botswana: A Development Success
Explore map of Obama’s supporter network.

I must say you have very interesting articles here. Your blog should
go viral.